ALERT: Docusign phishing attack
Anatomy of today's Docusign phishing attack
Today I received an email from Docusign, requesting my signature on a City of Philadelphia Procurement contract. I don’t do business with the City of Philadelphia so I knew it wasn’t real, but I was curious about this vector of attack, so I played along.
What I discovered was a clever way of getting you to provide your Microsoft credentials via legitimate pages and a couple of redirects. Please read the rest to learn how the attackers attempted to gain my trust and trick me into giving out my Microsoft credentials.
The first step is the email that was sent from a legitimate 3rd party, Docusign, which is a platform frequently used to send documents for electronic signature.
Docusign.net is a legitmate domain. There are no red flags here (other than me not expecting a contract doc from the city of Philadelphia).
Clicking the Review Document button takes you to the legitimate Docusign site.
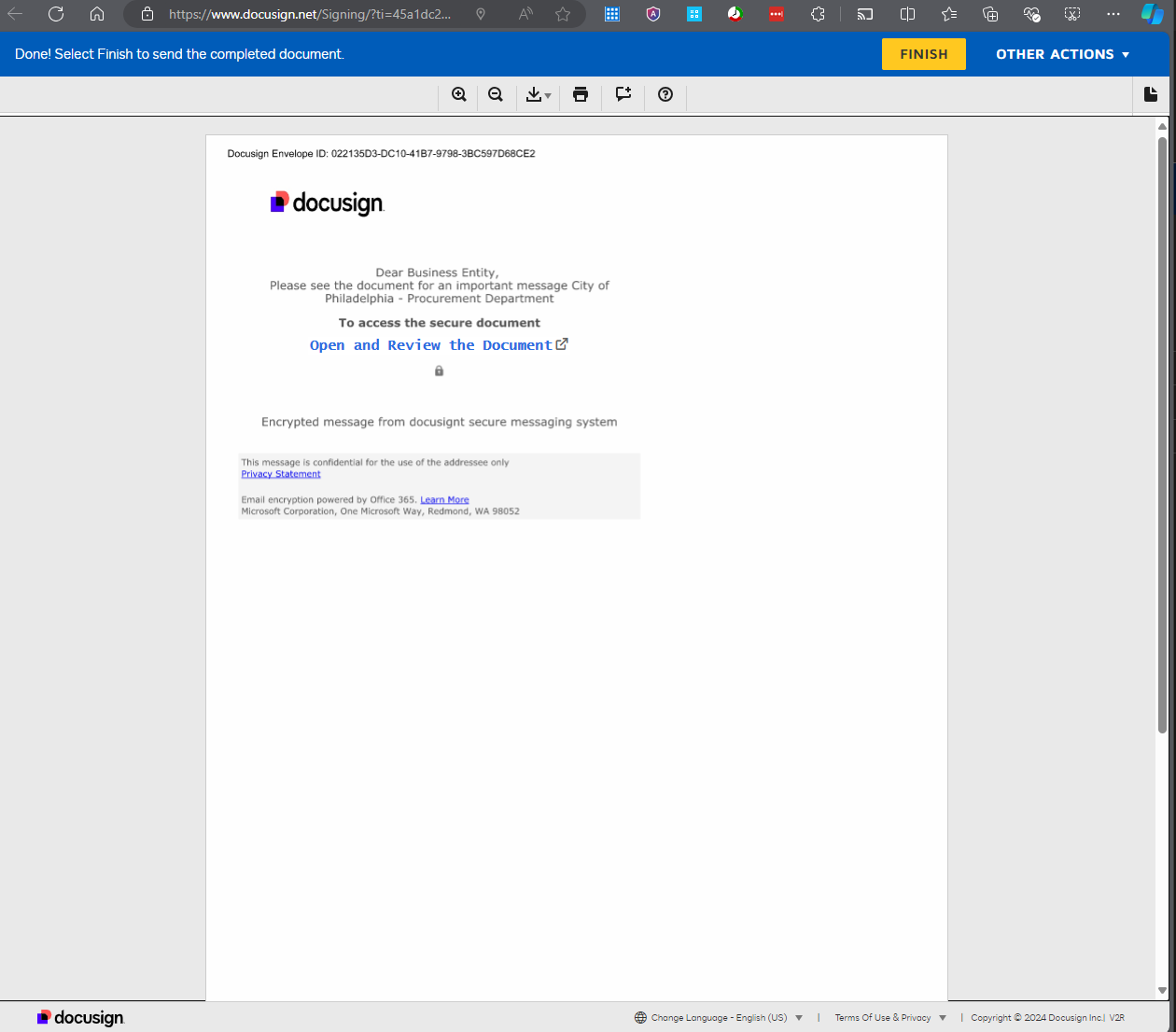
The document itself is a prompt to open the “encrypted document”, and if you’re not familiar with how Docusign is typically used, you may not think twice about clicking the link.
This page does have the usual red flags - such as incorrect spelling of DocuSign (“docusignt”), plus the use of weird and inconsistent fonts.
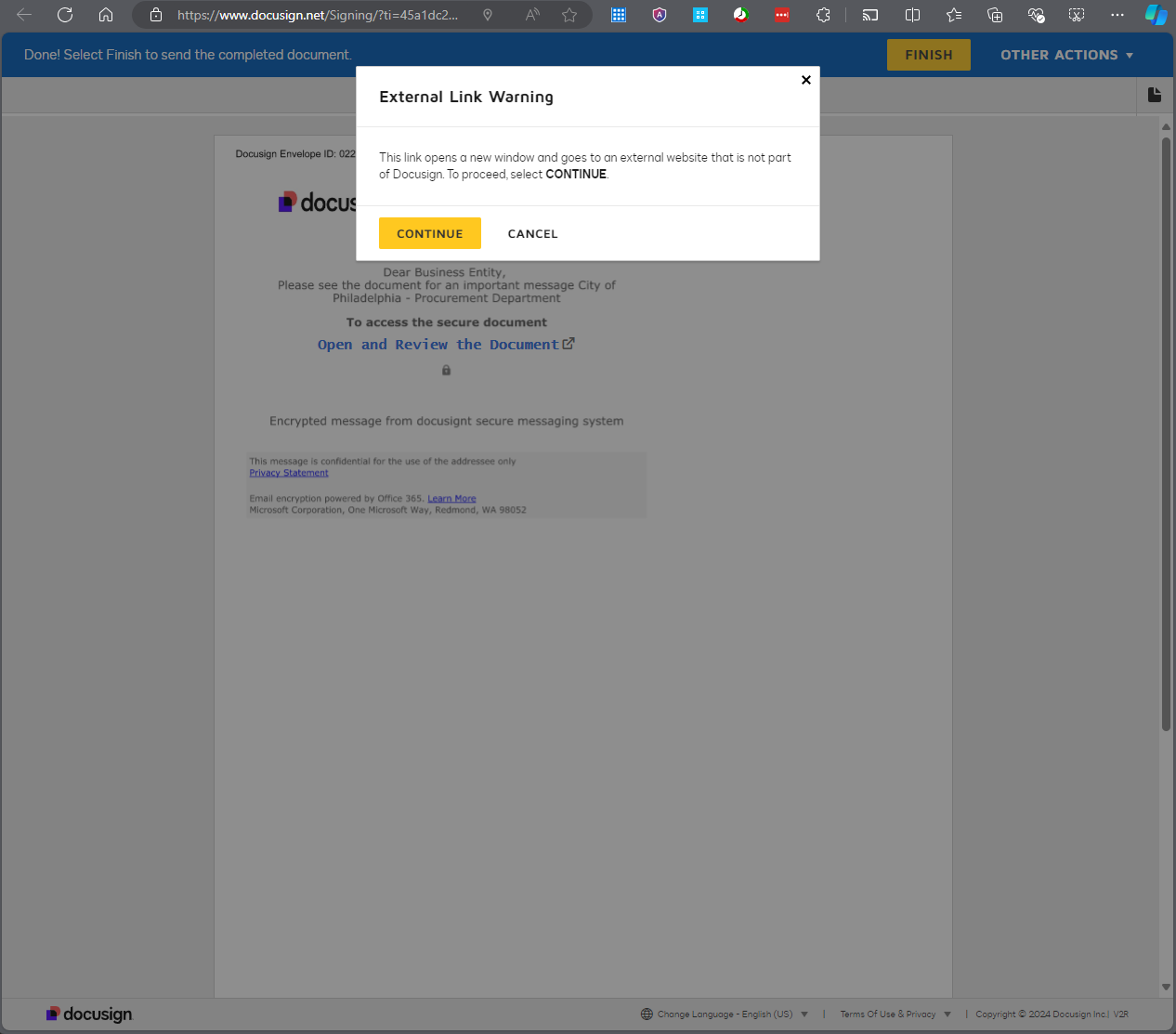
Clicking the Open and Review the Document link gives you the Docusign prompt about going to another page - which should be taken seriously.
The link takes you to another site, obviously NOT from a Microsoft domain (f1-telemetryo.ru, a Russian site), although it does a great job impersonating the Outlook open message screen:
which is then followed the Microsoft login screen:
If you enter your credentials here - bingo, the attacker now has your username and password. I didn’t continue past this point to see how they handle multi-factor authentication.
My suspicion is that they use a legitimate Microsoft authentication process to capture the authentication token after you yourself provide MFA to the sign-in page. If you do, the attackers will be able to bypass MFA and get access to your accounts. I’ve seen this happen, and this is how they get around the MFA protection.
If you get a similar looking message from Docusign (or another trusted 3rd party) - remain vigilant and pay attention to all the details such as spelling, URL, and so on. You should always err on the side of caution with all email you receive, and if there’s ever any doubt about the veracity of email or any sign-in link, triple-check the URL and reach out to your IT if you’re not 100% sure of its authenticity.
Stay safe, protect your digital identity and assets! If you have any questions, please give us a call.
Ilya Lehrman